How Crypto Scammers Use Bridges — and How You Can Protect Yourself

Recently, we came across an interesting case on Reddit. A user reported that money disappeared from their Phantom wallet on Solana.
The story looked typical: first, a small SOL deposit appeared in the wallet, then an automatic swap from USDC to SOL happened, and soon after that the SOL was withdrawn to an unknown address. According to the commentators, part of the stolen funds was later sent to an address connected to a bridge called Bridgers.
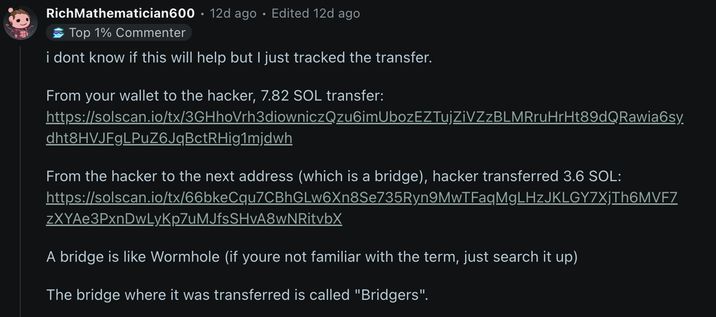
In general, it looks like a classic “cash-out” pattern: a small deposit for gas → token swap → withdrawal → transfer through a bridge.
In this article, we’ll look at how this works, why scammers use bridges, and what you can do to protect your wallet.
Why Bridges Became a Key Tool for Crypto Scammers
A bridge is a blockchain protocol that allows users to transfer tokens between different networks.
There are several main models:
- Lock-and-mint: tokens are locked in the source blockchain, and new wrapped tokens are issued on the target chain.
- Liquidity or relay bridges: assets are moved through liquidity pools and relay operators.
For regular users, bridges are a convenient way to move liquidity between blockchains without selling and rebuying tokens. However for scammers, they are extremely useful for two main reasons.
- Changing context: when funds move through a bridge, the blockchain, addresses, and transaction formats change. Simple tracking inside one network becomes almost impossible.
- Mixing and splitting: many bridges use liquidity pools or several routing addresses, which helps split and mix transactions — perfect for hiding stolen funds.
Because of this, bridges are now often part of “cash-out” schemes where hackers move stolen crypto into other networks to erase the trail and quickly exchange it for other assets or fiat.
Why Bridges Help Scammers Disappear
- Bridges don’t hack wallets — but they make it much easier for thieves to disappear.
- Cross-chain transfers change how funds look on-chain. Once money moves to another network, basic explorers and tools for the original blockchain stop being useful.
- Bridges also have internal routing and liquidity systems that naturally mix funds from many users, making tracing very difficult.
- Some bridges are even partially centralized, which adds extra risks.
- History shows that even large bridges, such as Wormhole, have been exploited for hundreds of millions of dollars — and hackers later used other bridges to move the stolen assets further.
How Wallet Hacks Usually Happen
The first goal of the attacker is to gain access to the victim’s wallet. This can happen in several ways:
Phishing: a fake website or app that asks for your seed phrase or private key.
Malware: keyloggers or trojans on a compromised computer or smartphone.
Fake or compromised wallet extensions: malicious updates or pop-ups asking you to “sign” a transaction.
Old permissions: previously approved smart contracts that can still move tokens without your confirmation.
Once the attacker can sign transactions, everything happens very fast.
They often send a small SOL deposit to cover transaction fees or activate automated scripts. Then, they perform a swap (for example, USDC → SOL) using a DEX router like Jupiter to convert everything into one liquid asset. After that, they send the SOL to their own address and immediately transfer part of it to a bridge address.
From there, the bridge transfers or mints the tokens on another blockchain, changing the addresses and networks. The funds are then often split, sent through different smart contracts, or moved to centralized exchanges with KYC to try to cash out.
How to Spot the Signs of a Wallet Compromise
If you monitor your wallet activity, there are several red flags to look for:
- A small incoming SOL deposit before several automatic outgoing transactions.
- A sudden swap through an aggregator like Jupiter.
- Transfers to addresses linked to bridges.
- Several small transactions made within minutes.
- A quick attempt to send funds to known exchanges.
If you see this pattern, your keys were most likely compromised, or a smart contract still has permission to move your funds.
What to Do If You Notice Suspicious Transactions
- Save evidence. Write down or screenshot all transaction IDs, wallet addresses, times, and balances before and after the theft.
- Contact wallet support immediately. For example, Phantom has an official form for reporting scams.
- Report to law enforcement. In the U.S., you can use the FBI’s IC3 portal; in other countries, contact your local cybercrime unit.
- Notify blockchain analytics firms such as Arkham, Chainalysis, or Elliptic. They can track the stolen funds and warn exchanges if the assets reach a KYC platform.
- Protect your remaining funds. If you still have tokens in the same wallet, do not move them from a possibly infected device. Create a new wallet on a clean computer or, better yet, use a hardware wallet.
- Get a forensic check. Cybersecurity experts can scan your devices for malware, keyloggers, or fake extensions.
- Avoid fake recovery offers. Never send your seed phrase to anyone who claims they can “get your money back.”
Final Thoughts
Bridges are a great tool in decentralized finance — they connect blockchains and make liquidity flow freely. But they’ve also become a favorite instrument for criminals. Bridges don’t cause wallet hacks, but they make it much easier to hide stolen crypto and move it across networks.
The real danger still lies in key compromise and unsafe approvals. Protect your seed phrase, keep your funds offline when possible, and use trusted devices. If a hack does happen, document everything and reach out to wallet support, forensic analysts, and law enforcement right away.
Fast action and good security habits are your best defense.