How to Keep Your Crypto Assets Safe at the Right Place

Recent Cyber Attacks
Since the foundation of cryptography in 2009, the graph of digital money has been fluctuating. With a presiding rise in the trading value of cryptocurrency in the past four years, Crypto assets have become a ceaseless temptation to the investors and doubtlessly to the cyber criminals. The biggest crypto robbery of 2019 has been eye-opening for crypto exchanges and central authorities. Again in the year 2021 one of the biggest crypto heist recorded the theft of $267m Ether currency, $252 of Binance coins and approximately $85m in USDC tokens from blockchain site, Poly Network. It was regarded as a huge economic crime. The respective attacker was forced by Poly to return all the money as many masses have invested their whole life savings. Once again it put a huge question on the security of crypto assets.
How to Keep the Exchanges and Wallets More Secure?
Keeping your crypto assets safe is directly linked to keep your wallets secure.
Investors’ lack of awareness about crypto currency safety precautions and the insufficient security provided by the exchanges, brokerages and crypto wallets results in cyber-attacks. This aroused the need:
- To make exchange accounts or digital wallets more secure.
- To guide the capitalists with necessary information while handling digital wallets.
- To choose the right storage to securely store crypto assets.
1. Keys To Enhance The Protection of Exchange Accounts, Digital or Custodial Wallets
i. Choosing a reliable cryptocurrency exchange
Safety of the crypto-assets should be a top-priority while choosing a crypto exchange.
It is said that old is gold. This is very much related while choosing a reliable crypto exchange. The older cryptocurrency exchanges are considered to be the safest.
Top 3 Crypto Exchanges
Below are the top 3 secure cryptocurrency exchanges that have been listed from top to bottom.
Coinbase - the first ever crypto exchange, launched in 2012, and is considered to be the most secure crypto platform because it saves 98% of the cryptocurrency in cold storage; only 2% is utilized in online trading.
Supporting almost 50 cryptocurrencies, free wallet, and access to private key and easy user interface makes it popular among beginners and long term investors.
Gemini - offers similar features like coin base, saves majority of its cryptocurrency in cold storage and the least are kept for online dealings. Unlike coinbase, it supports up to 40 crypto currencies.
Etoro - supports up to 20 coins and the coins are secured in cold and hot wallets under the custody of FDIC. This crypto exchange is attractive because of its unique virtual portfolio feature which allows the imaginary implementation of investing up to $100,000 valued crypto for practice. This gave a clear picture how a particular cryptocurrency fluctuates.
ii. Application of Strong Password
Since the private keys to access the crypto assets are secured in the custodial wallet of your online crypto account, the demand of using a strong complicated password is very high to prevent any unauthorized online access. If you lost your key, you lost all of your funds. The account security should be assured with long uncrack able password to prevent any unauthorized access to the key.
Example
You should use a long and complex password like this;
WTnf$45De7dxPRT6pmxLcF6&QxtGWvh&N3bTeSHR
Befj8qn#iOo#@BACINQ2LWZJ23Q7ElwHNZ%xWp3e
Clearly you cannot memorize this password. You can write it on paper or secure it in a hard drive or store it in the password manager.
iii. Use Multiple Passwords for Multiple Accounts
Mostly it is seen that the same password is assigned to multiple digital accounts. Whether it’s a website, Gmail or various social media accounts, same password is set up. This makes a smoother path for hackers to track your identity and credentials. Use multiple passwords for not just multiple crypto accounts but also for other digital accounts. Securing multiple passwords is an important task and it can easily be done with a password manager. Secure your long, complex multiple passwords in the password manager and apply a master password to save all these passwords. The master password should be extremely complicated and difficult to crack.
Top 3 Password Managers
- KeePass2
- Bit Warden
- 1Password
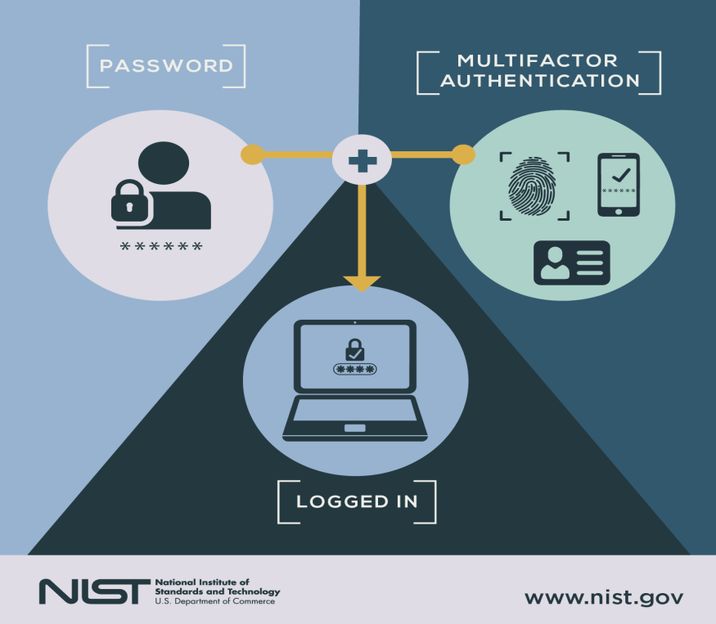
iv. Use 2 Factor Authentication (2FA)
Your username and password are the first two credentials that will protect your crypto account. Even this 32 lettered identifier and complicated password can sometimes fail to protect your crypto information and assets, A 2FA (factor authentication code) is needed to make it more secure. It serves as a 3rd strong credential to access your digital wallet. It is a one-time use code, each time you login a new code is generated.
You can set up the 2FAcode in the security section of your wallet through:
- Google authenticator app to generate codes
- Yubikey (a hardware authentication-device)
- Through receiving SMS to phone.
Setting up a 2FA surely minimizes the risk to cyber-attacks as if the hacker who gets access to your password or wallet ID won’t be able to login due to unique 2FA code that is changed with every login attempt.
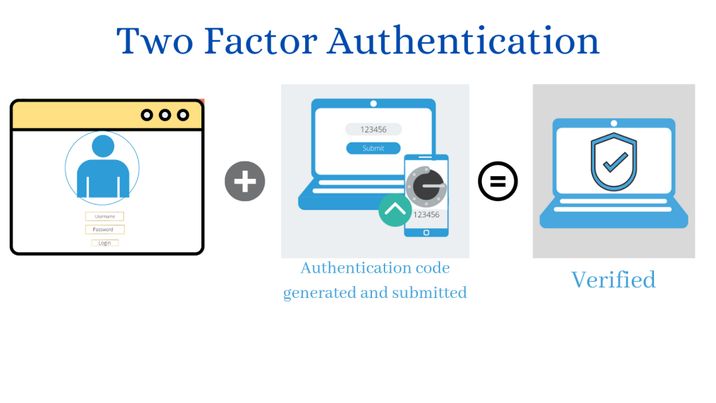
Note: Google authenticator app is considered to be the safest. The app over rules the later authentication methods because it’s free of cost besides every 30 seconds a new code is generated to bypass any delays.
v. Use Multi Factor Authentication aka MFA
Multi Factor Authentication serves as 4th powerful credential to further protect your crypto wallet. It involves the verification of instantly produced identifiers like a pin code and a fingerprint to access your account or wallet.
2. Observe Other Safety Measures While Handling Digital Wallets
i. Device should be virus free
Mostly the importance of anti-virus and system updates is overlooked. To secure online trading of cryptocurrency, a good antivirus program which updates its features regularly should be installed on the respective device-used for crypto operations. The anti-virus should be lightweight, efficient and must offers following features:
- Powerful web and data protection to ensure secure currency exchanges
- Ransomware shield- to prevent the encryption of your files without your permission.
- Can blacklist an app or operation you don’t trust.
- Secure line VPN features to hide your presence by concealing your IP and encrypting online browsing with a 256 AES- bit technology during interactive crypto transactions.
- Artificial intelligence and machine learning to combat any spy or malware attack.
- Protecting browsers by filtering or rectifying the URLs and scrutinizing the downloaded content.
Thus anti-virus comes up with necessary traits you need to stay safe and protected while you are online or offline.
Top Rated Anti-Virus Software
- ESET
- Avira
- Bull guard
- Bit defender
- VIPRE
ii. Regular software updates
If your system is regularly updated with the latest software updates, your device wallet is less likely to get liable to malware attacks. The newest updates come with the latest security measures to protect you from the strong scams aiming to corrupt or steal your crypto assets.
iii. Don’t share your login credentials
Never ever share your login credentials with anyone online or in person. Store your private key on physical paper and keep it highly confidential.
iv. Avoid public networks
Using public networks for crypto transactions can surely put you in big trouble. Even through your home network, use a VPN while trading on crypto exchange. VPN changes your IP address and location so you can browse securely without fear of being hacked.
v. Check the URLs
Hackers make fake websites to trap you. Double check the URLs before clicking any link.
vi. Don’t get scammed
The malicious ads are the easy ways of crypto-jacking that can steal all your crypto by just one click. To save you from scammers don’t click on any link without verification and trust anyone or any organization online- apparently looking trustworthy, demanding payments in crypto only. Close all the tabs of the browser after use. Enable Ad Blocker Plus and browser extensions to minimize the appearance of blocks.
3. Which One is the Right Storage to Secure Your Crypto Assets?
Crypto or Non-custodial Wallets
i. Cold Wallets
Non-custodial wallets are cold wallets that are small devices connected to computers or laptops. These wallets work offline and go online only for a limited time period for trading stored crypto funds. Once the device is plugged out of the computer nobody can harm or access the program files that directly link to your stored coins or tokens unless it gets stolen or gets access by any illegitimate practice. Paper wallet, USB storage devices are the most secure form of cold wallets. Cold storage devices are fully encrypted physical devices, functions offline with no custody of third parties. The offline private keys can only be accessed by the owner of the assets.
Now there are multiple options in cold wallets: hardware wallets and paper wallets.

ii. Hardware Wallets
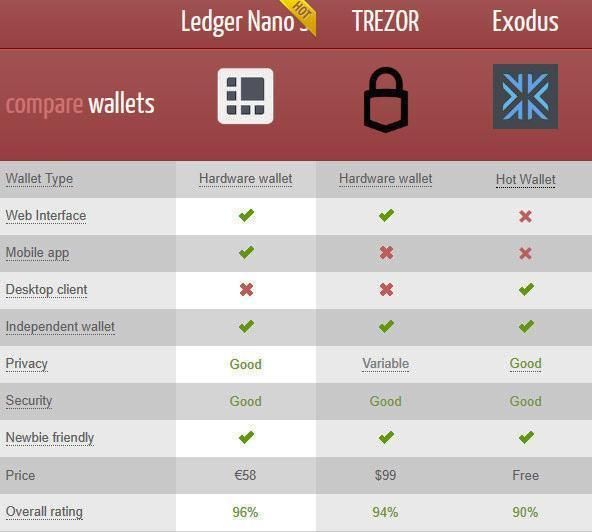
Hardware wallets are simply USB-like storage devices. Ledger hardware wallets are easy to use by storing your private keys on an integrated chip to ensure the security. Electrum, Zengo, Exodus, Trezor, Ledger Nano S and Ledger Nano X are best choices as they work with a combination of Secure Element and a proprietary operating system. Furthermore, in case if the device gets stolen or lost, a 24 word backup recovery phrase can save the owner from big loss. Nano X is larger than Nano S, supports up to 100 applications and comes with Bluetooth technology.
Security with Handiness
- Ledger is the only attested hardware wallet available in the market and certified by the French cyber security, ANSII. The features like SE (secure element), custom operating system (BOLOS) and legitimate authentication process serves as a secure shield to private keys and protect against malicious attacks or any unauthorized access.
- The Live ledger app helps to keep everything transparent for you. Every transaction takes place in front of your screen. The online application allows you to control your crypto operations from your phone or laptop. It supports up to 1800+coins and other external crypto services.
- Ledger Nano X is dominant over Ledger Nano S as it supports up to 100 applications and comes with Bluetooth technology.
iii. Paper Wallets
It is a printed QR code on a physical piece of paper. It can be used to execute digital money exchanges. They are not prone to online attacks but are very much likely to get misplaced. No participation in partial transactions made them insignificant compared to cold wallets.
iv. Hot Wallets
It is a form of digital storage that can be accessed through mobile or desktop. Hot wallets or software wallets are directly connected to the web server. These wallets are free of cost and convenient to use because of direct internet, user friendly interface and efficiency. Mobile devices, laptops and desktops all lie in the hot wallet list as exchange of cryptocurrency is easy and efficient with online connection. In regards to safety, hot wallets fail to match the standards because they are more liable to online attacks. Hot wallets mainly entitle the online financial transactions instead of storing digital currencies.
v. Mobile and Desktop wallets
These wallets are basically software that are installed on computers and deal with viruses to avoid any online connection. A private key comes with these wallets stored in a virtual layer. Bitcoin core, electrum, exodus, MetaMask, MyEtherWallet, MyCryptoWallet are some examples.
Cold Wallet vs. Hot Wallet: Which One is a Better Choice
Cold wallets are the best place to secure your crypto assets. Due to direct internet connection, hot wallets are somewhat more prone to cyber-attacks. The set of public and private keys are stored in a program that is also connected to the internet with a certain warning for crypto assets. Cold wallets are not connected to the internet. The private keys are secured offline and are less likely to get attacked by any illegal action.
Conclusion
To sum up, the safety of crypto assets depends upon the safety of crypto wallets. In case of custodial wallets, the funds are under the custody of central authority or crypto exchange. The security of funds revolves around the protection of online account credentials. A powerful complex password along with 2FA (factor-authentication) and MFA (Multi-Factor Authentication) serves as a strong shield against spammers or any illegal act.
In case of non-custodial wallets, the management, storage and security of crypto assets all lies under the owner’s control. The access and transfer of assets are verified through private keys. So private keys should be kept and guarded with utmost care. Using hardware wallets, regular backups, software updates and essential security measures can save your funds from getting hacked or stolen.